Updated on 18 Feb, 2025
Master File Table ($MFT):
The MFT is a database that stores information about every file and directory on an NTFS volume. It's essentially a metadata repository, containing records for each file, including its attributes and metadata.
Understand the $MFT and there structure check out below article:

Collection:
Investigation with Kape.
We'll use KAPE to acquire the NTFS Master File Table ($MFT) and journals. Then, we'll employ MFTECmd to parse the MFT.
Kape triage compound target, showcasing snippets of the MFT, $J, and link files targets. The output structure of Kape, with raw files and parsed outputs, is detailed, emphasizing the efficiency of this workflow in gathering artifacts for analysis.
Kape can be used as GUI version or Cmd version its depend upon your preference need.
command
----------------------------------------------------------------------------------------------------
Parsing:
There is complete article written regarding parsing of $MFT using MFTExplorer/MFTECMD check out below
----------------------------------------------------------------------------------------------------
Analyzing:
Column Headers:
As we begin our exploration, take note of the extensive list of column headers. These headers provide essential information about MFT entries, including file names, sizes, and crucially, timestamps.
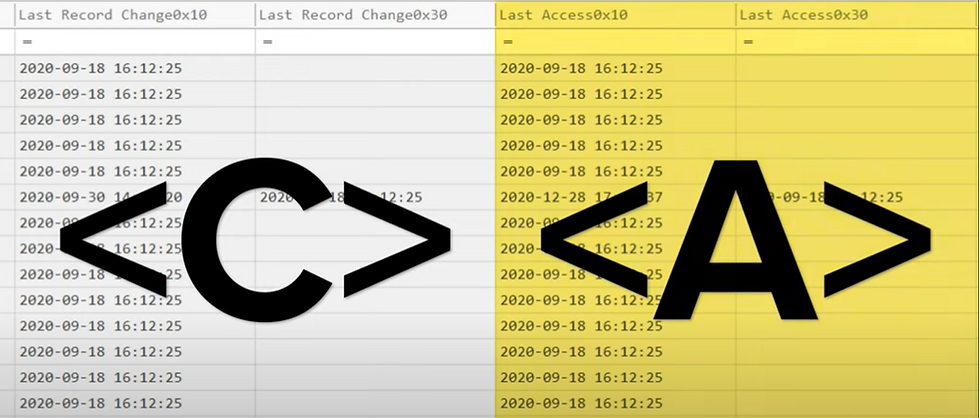
Understanding Timestamps:
Each timestamp column corresponds to specific aspects of file operations, such as creation (B), modification (M), and access (A). The timestamps are presented in a hex format.
with hex 0x10 denoting $SI
while hex 0x30 represents $FN----------------------------------------------------------------------------------------------------
Detecting Time Stomping
Time stomping can be detected by comparing these two time stamp $SI and $FN we can identify time stomping.
You can learn more about Timestomping check out the article below:
----------------------------------------------------------------------------------------------------
Interpreting Blank Timestamps:
You may notice some blank timestamps in columns ending with hex 0x30. These blanks signify that the $file name timestamps are identical to the corresponding $standard information timestamps. This design choice reduces noise in the data and directs attention to entries where timestamps diverge, aiding in identifying suspicious activities.
---------------------------------------------Dean---------------------------------------------------------








Comments