Part 5- (WMI): Unveiling the Persistence of Malicious MOF Files: A Deep Dive into #PRAGMA AUTORECOVER
- Jan 17, 2024
- 2 min read
This blog explores the significance of a specific attribute within MOF files – “#PRAGMA AUTORECOVER” – shedding light on its forensic implications and the motivations behind its inclusion in malicious payloads.
Understanding #PRAGMA AUTORECOVER:
#PRAGMA AUTORECOVER primary purpose is to safeguard against potential data loss within the WMI repository. When this pragma is included, a copy of the MOF file is stored, ensuring that even if the WMI repository needs to rebuild itself, the original entries do not age out.
Forensic Artifacts and Detection:
In instances where #PRAGMA AUTORECOVER is part of a malicious MOF file, remnants of the file can be found within the
"C:\Windows\System32\wbem\AutoRecover"
This presents a valuable opportunity for cybersecurity professionals to identify and analyze potentially harmful introductions in the WMI database. The autorecover feature can also be triggered using the mofcomp.exe tool with the "-autorecover" parameter.
Analyzing the AutoRecover Folder:
Upon inspection of the "AutoRecover" folder, analysts may encounter renamed copies of MOF files, each containing a textual representation of the original entries. Although the original filename may not be evident, the timestamps (creation and modification) can be instrumental in identifying outliers. The presence of these files in the expected time range of an attack becomes a crucial indicator for further investigation.
Windows Registry Entry:
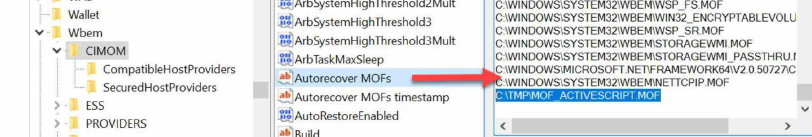
When #PRAGMA AUTORECOVER is utilized, a corresponding Windows Registry entry is generated in the
"HKLM\SOFTWARE\Microsoft\Wbem\CIMOM"
Under the "Autorecover MOFs" value, the recorded name includes the folder path where it existed during compilation. This information, coupled with the type of consumer (e.g., "ActiveScript"), serves as a valuable clue for investigators to scrutinize the AutoRecover folder files on disk.
Motivations Behind #PRAGMA AUTORECOVER in Malicious MOF Files:
The prevalence of #PRAGMA AUTORECOVER in malicious MOF files raises questions about the motives of threat actors. Ignorance of detection risks, combined with a desire to maintain persistence within compromised networks, likely drives the inclusion of this pragma. Considering that MOF files primarily serve the purpose of persistence, they become a crucial avenue for threat actors to regain access to compromised systems.
Conclusion:
As cybersecurity professionals strive to stay ahead of evolving threats, understanding the nuances of techniques employed by threat actors is paramount. The exploration of #PRAGMA AUTORECOVER within malicious MOF files emphasizes the importance of proactive detection, analysis, and mitigation strategies.
Akash Patel

Comments