macOS Incident Response: Tactics, Log Analysis, and Forensic Tools
- Oct 10, 2024
- 5 min read

macOS logging is built on a foundation similar to traditional Linux/Unix systems, thanks to its BSD ancestry. While macOS generates a significant number of logs, the structure and format of these logs have evolved over time
----------------------------------------------------------------------------------------------
Overview of macOS Logging
Most macOS logs are stored in plain text within the /var/log directory (also found as /private/var/log).
These logs follow the traditional Unix Log Format:
MMM DD HH:MM:SS HOST Service: MessageOne major challenge: log entries don't include the year or time zone, so when reviewing events near the turn of the year, it’s important to be cautious.
Logs are rotated based on size or age, with old logs typically compressed using gzip or bzip2.
Key Difference from Linux/Unix Logging
macOS uses two primary binary log formats:
Apple System Log (ASL): Introduced in macOS X Leopard, ASL stored syslog data in a binary format. While deprecated, it’s still important for backward compatibility.
Apple Unified Log (AUL): Starting with macOS Sierra (10.12), AUL became the standard for most logging. Apps and processes now use AUL, but some data may still be logged via ASL.
----------------------------------------------------------------------------------------------
Common Log Locations
Investigators should know where key log files are stored:
/var/log: Primary system logs.
/var/db/diagnostics: System diagnostic logs.
/Library/logs: System and application logs.
~/Library/Logs: User-specific logs.
/Library/Application Support/(App name): Application logs.
/Applications: Logs for applications installed on the system.
----------------------------------------------------------------------------------------------
Important Plain Text Logs
Some of the most useful plain text logs for enterprise incident response include:
/var/log/system.log: General system diagnostics.
/var/log/DiskUtility.log: Disk mounting and management events.
/var/log/fsck_apfs.log: Filesystem-related events.
/var/log/wifi.log: Wi-Fi connections and known hotspots.
/var/log/appfirewall.log: Network events related to the firewall.
Note: Starting with macOS Mojave, many of these logs have transitioned to Apple Unified Logs (AUL). On upgraded systems, you might still find them, but they are no longer actively used for logging in newer macOS versions.
----------------------------------------------------------------------------------------------
Binary Logs in macOS
macOS has shifted toward binary logging formats for better performance and data integrity. Investigators should be familiar with two main types:
1. Apple System Logs (ASL)
Location: /var/log/asl/*.aslView: Use the syslog command or Console app during live response.
ASL contains diagnostic and system management data, including startup/shutdown events and some process telemetry.
2. Apple Unified Logs (AUL)
Location:
/var/db/diagnostics/Persist
/var/db/diagnostics/timesync
/var/db/uuidtext/File Type: .tracev3
AUL is the default logging format since macOS Sierra (10.12). These logs cover a wide range of activities, from user authentication to sudo usage, and are critical for forensic analysis.
How to View AUL:
View in live response: Use the log command or the Console app.
File parsing: These logs are challenging to read manually. It’s best to use specialized tools designed to extract and analyze AUL logs.
----------------------------------------------------------------------------------------------
Limitations of macOS Logging
Default Logging May Be Insufficient: Most macOS systems don’t have enhanced logging enabled (like auditd), which provides more detailed logs. This can result in gaps when conducting enterprise-level incident response.
Log Modification: Users with root or sufficient privileges can modify or delete logs, meaning attackers may tamper with evidence.
Binary Format Challenges: Analyzing ASL and AUL logs on non-macOS systems can be difficult. The best approach is to use a macOS device for live response or log analysis, as using other platforms may result in a loss of data quality.
----------------------------------------------------------------------------------------------
Live Log Analysis in macOS
1. Using the Last Command
Just like in Linux, the last command shows the most recent logins on the system, giving investigators a quick overview of user access.
2. Reading ASL Logs with Syslog
The syslog command allows investigators to parse Apple System Log (ASL) files in binary format:
syslog -f (filename).aslWhile it can reveal key system events, it’s not always easy to parse visually.
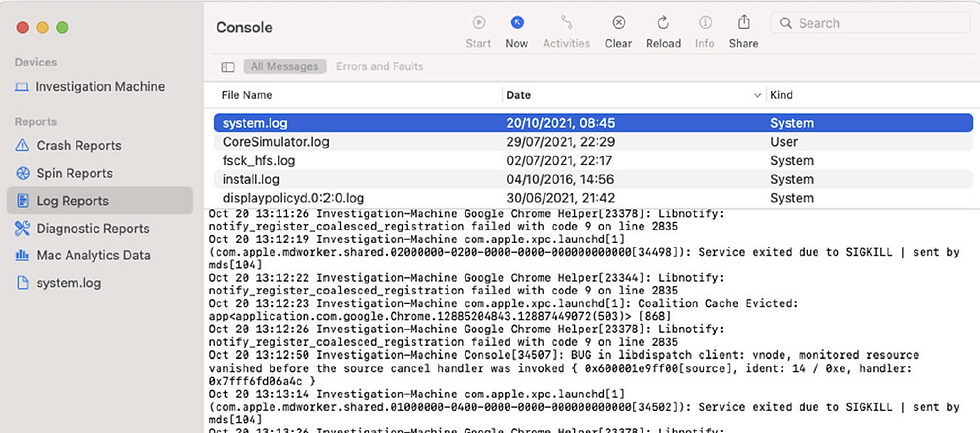
3. Live Analysis with the Console App
For a more user-friendly experience, macOS provides the Console app, a GUI tool that allows centralized access to both Apple System Logs (ASL) and the more modern Apple Unified Logs (AUL). It’s an ideal tool for visual log analysis, but keep in mind, you can’t process Console output with command-line tools or scripts.
----------------------------------------------------------------------------------------------
Binary Log Analysis on Other Platforms
When you can’t analyze logs on a macOS machine, especially during forensic analysis on Windows or Linux, mac_apt is a powerful, cross-platform solution.
mac_apt: macOS Artifact Parsing Tool
Developed by Yogesh Khatri, mac_apt is an open-source tool designed to parse macOS and iOS artifacts, including Apple Unified Logs (AUL).
Key Features:
Reads from various sources like raw disk images, E01 files, VMDKs, mounted disks, or specific folders.
Extracts artifacts such as user lists, login data, shell history, and Unified Logs.
Outputs data in CSV, TSV, or SQLite formats.
Challenges with mac_apt:
TSV Parsing: The default TSV output is in UTF-16 Little Endian, which can be tricky to process with command-line tools. However, it works well in spreadsheet apps.
Large File Sizes: Log files can be huge, and mac_apt generates additional copies for evidence, which can take up significant disk space. For example, analyzing a 40GB disk image could produce a 13GB UnifiedLogs.db file and 15GB of exported evidence.
Speed: Some plugins can be slow to run. Using the FAST option avoids the slowest ones but can still take 10-15 minutes to complete. A full extraction with plugins like SPOTLIGHT and UNIFIEDLOGS can take over an hour.
----------------------------------------------------------------------------------------------
How to Use mac_apt
The command-line structure of mac_apt is straightforward, and you can select specific plugins based on the data you need:
python /opt/mac_apt/mac_apt.py -o /output_folder --csv -d E01 /diskimage.E01 PLUGIN_NAMEFor example, to investigate user activity:
python /opt/mac_apt/mac_apt.py -o /analysis --csv -d E01 /diskimage.E01 UTMPX USERS TERMSESSIONSThis will extract user information, login data, and shell history files into TSV files.
Useful mac_apt Plugins for DFIR:
ALL: Runs every plugin (slow, only use if necessary).
FAST: Runs plugins without UNIFIEDLOGS, SPOTLIGHT, and IDEVICEBACKUPS, speeding up the process.
SUDOLASTRUN: Extracts the last time sudo was run, useful for privilege escalation detection.
TERMSESSIONS: Reads terminal history (Bash/Zsh).
UNIFIEDLOGS: Reads .tracev3 files from Apple Unified Logs.
UTMPX: Reads login data.
----------------------------------------------------------------------------------------------
Conclusion:
Tried to simplifies the complex task of macOS log analysis during incident response, providing investigators with practical tools and strategies for both live and binary log extraction. By using the right tools and understanding key log formats, you can efficiently gather the information you need to support forensic investigations.
Akash Patel

Comments