M365 Logging: A Guide for Incident Responders
- Oct 16, 2024
- 3 min read

When it comes to Software as a Service (SaaS), defenders heavily rely on the logs and information provided by the vendor. For Microsoft 365 (M365), the logging capabilities are robust, often exceeding what incident responders typically find in on-premises environments. At the heart of M365’s logging system is the Unified Audit Log (UAL), which captures over 100 different activities across most of the SaaS products.
What You Get: Logs and Retention Periods
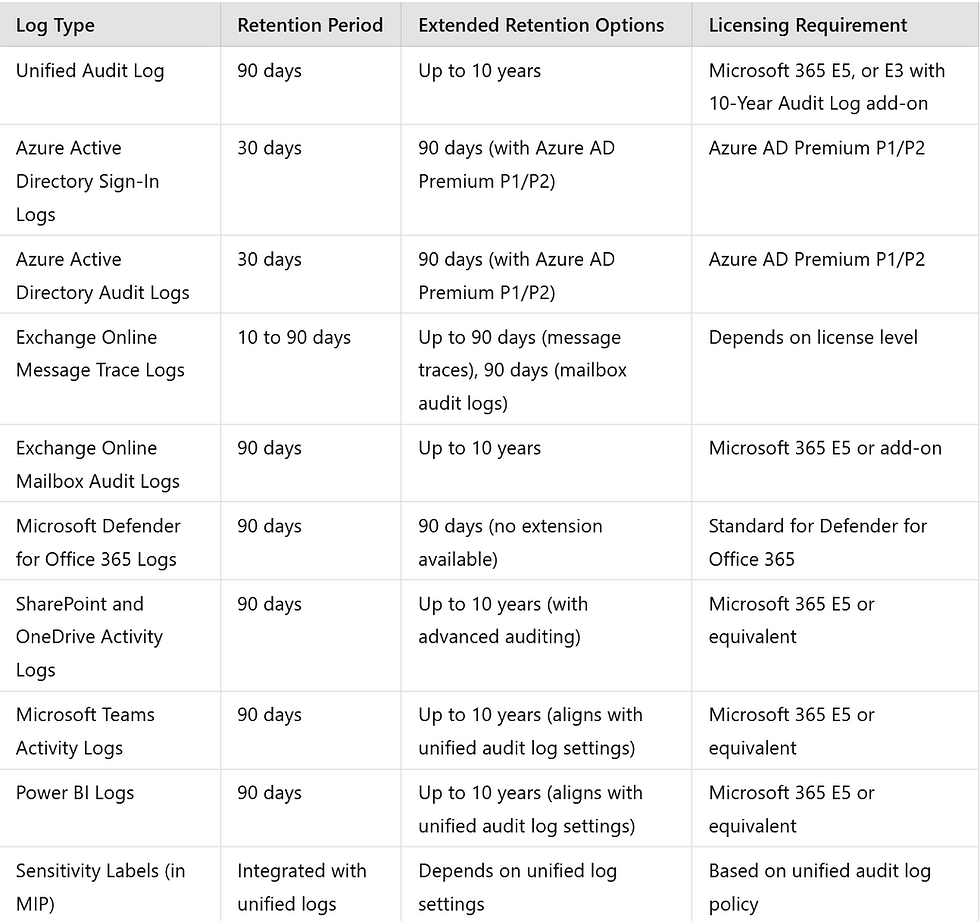
The type of logs you have access to, and their retention periods, depend on your M365 licensing. While there are options to extend retention by offloading data periodically, obtaining the detailed logs available with higher-tier licenses can be challenging with less expensive options.
Another consideration is the limitations Microsoft places on API quotas for offloading and offline analysis. However, there are ways to navigate these restrictions effectively.
Log Retention Table: (It kept on updating by Microsoft so keep an eye on Microsoft)
Key Logs in M365
Azure AD Sign-in Logs:
Most Microsoft services now use Azure Active Directory (AD) for authentication. In this context, the Azure AD Sign-in logs can be compared to the 4624 and 4625 event logs in on-premises domain controllers.
A unique aspect of these logs is that most authentication requests originate from the internet through publicly exposed services. This allows for additional detection methods based on geolocation data.
The information gathered here is also ideal for time-based pattern analysis, enabling defenders to track unusual login behaviors.
Unified Audit Log (UAL):
The UAL is a treasure trove of activity data available to all paid enterprise licenses. The level of detail varies by licensing tier, and Microsoft occasionally updates what each package includes.
Unlike typical Windows logs, where a significant percentage may be irrelevant to incident response, the UAL is designed for investigations, with almost all logged events being useful for tracing activities.
Investigation Categories
To help incident responders leverage the UAL effectively, we categorize investigations into three types: User-based, Group-based, and Application-based investigations. Each category will include common scenarios and relevant search terms.
1. User-Based Investigations
These investigations focus on user objects within Azure AD. Key activities include:
Tracking User Changes: Understand what updates have been made to user profiles, including privilege changes and password resets.
Auditing Admin Actions: Log any administrative actions taken in the directory, which is crucial for accountability.
Typical Questions:
What types of updates have been applied to users?
How many users were changed recently?
How many passwords have been reset?
What actions have administrators performed in the directory?
2. Group-Based Investigations
Group-based investigations are closely related to user investigations since permissions in Azure AD often hinge on group memberships. Monitoring groups is vital for security.
Group Monitoring: Track newly added groups and any changes in memberships, especially for high-privilege groups.
Typical Questions:
What new groups have been created?
Are there any groups with recent membership changes?
Have the owners of critical groups been altered?
3. Application-Based Investigations
Application logs can vary significantly depending on the services in use. One critical area to investigate is application consent, which can highlight potential breaches if an attacker gains access through an Azure application.
Typical Questions:
What applications have been added or updated recently?
Which applications have been removed?
Has there been any change to a service principal for an application?
Who has given consent to a particular application?
4. Azure AD Provision Logs
Azure AD Provision logs are generated when integrating third-party services like ServiceNow or Workday with Azure AD. These services often facilitate employee-related workflows that need to connect with the user database.
Workflow Monitoring: For instance, during employee onboarding in Workday, the integration may involve creating user accounts and assigning them to appropriate groups, all of which are logged in Azure AD Provision logs.
Typical Questions:
What groups have been created in ServiceNow?
Which users were successfully removed from Adobe?
What users from Workday were added to Active Directory?
Leveraging Microsoft Defender for Cloud Apps
The Microsoft Defender for Cloud Apps can be an invaluable tool during investigations, provided it is correctly integrated with your cloud applications. By accessing usage data, defenders can filter out certain user agents and narrow down the actions of an attacker.
For more information, refer to Microsoft Defender for Cloud Apps Announcement.
Conclusion
Understanding and effectively utilizing the logging capabilities of M365, particularly the Unified Audit Log and other related logs, can significantly enhance your incident response efforts. By focusing on user, group, and application activities, defenders can gain valuable insights into potential security incidents and make informed decisions to bolster their security posture.
Akash Patel

Comentários