Lateral Movement in Cyber Attacks: Key Protocols, Tools, and Detection Methods
- Aug 27, 2024
- 4 min read
Lateral movement refers to how attackers move through a network after gaining initial access. This allows them to explore the environment, escalate privileges, and reach their final target, often sensitive data or critical systems. Lateral movement is hard to track due to the variety of methods used.
Common Lateral Movement Protocols
Server Message Block (SMB):
Used for file sharing over the network.
TCP ports 137, 138, 139, and 445 are utilized.
Tools: PsExec (SysInternals), smbexec (Impacket).
Event IDs to monitor:
5140: A network share object was accessed.
4688/4689: Process creation (Sysmon Event IDs 1 / 5).
7045/7036: Service creation and status changes.
Remote Desktop Protocol (RDP):
Enables remote access to systems.
Attackers often add themselves to the “Remote Desktop Users” group.
Monitor for Event ID 4728: "A member was added to a security-enabled global group".
RDP Cached Bitmaps:
RDP clients store 64x64-pixel bitmap tiles, which are cached by default.
These cached images can be obtained and parsed for forensic analysis.
I have created an complete blog to analyze RDP Cached Bitmaps (Do check it out to learn more Link below)
Windows Remote Management (WinRM):
Microsoft’s implementation of the WS-Man protocol.
WinRS (Remote Shell) is commonly used in ransomware campaigns.
Monitoring:
Check for command lines such as winrs.exe -r:target /username:admin /password:pass.
Tools like SharpSphere can compromise vSphere infrastructure through WinRM.
Windows Management Instrumentation (WMI):
Allows for administrative tasks on remote systems.
Often abused by ransomware operators to execute commands or transfer files.
Background Intelligent Transfer Service (BITS):
Used for downloading files in the background.
Attackers utilize BITS for stealthy data transfers and task execution.
Tools Commonly Used for Lateral Movement
Ransomware operators and threat actors use a variety of scanners to identify targets for lateral movement:
Advanced IP Scanner
Advanced Port Scanner
Angry IP Scanner
Cobalt Strike (built-in scanning capabilities)
KPort Scanner
nmap
Qfinder Pro
SoftPerfect Network Scanner
Detailed Protocol Insights
Server Message Block (SMB)
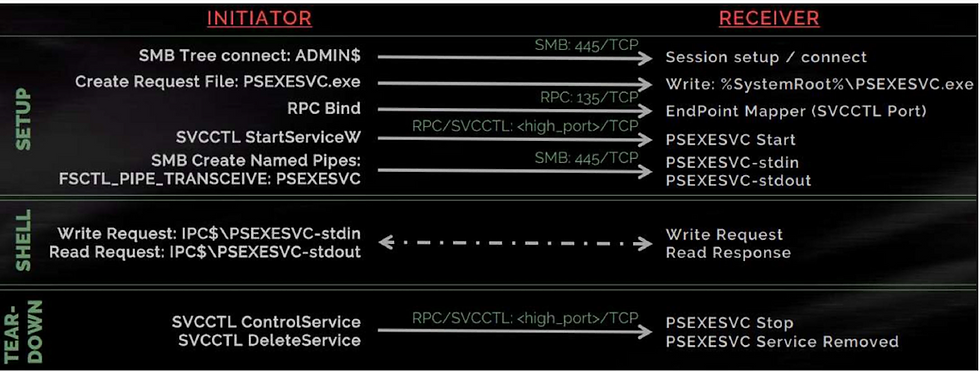
SMB is a primary target for lateral movement. PsExec, for instance, is a popular tool for running processes remotely:
PsExec Process:
Opens an SMB session to the target.
Uploads PSEXESVC.exe to the ADMIN$ share.
Creates a named pipe(Example:- \\client\pipe\svcctl) to talk to the Service Control Manager (SCM).
Calls CreateService using the newly uploaded PSEXESVC.exe as ImageFile.
Calls StartService to run the service.
Detection:
File Creations: Monitor for the creation of PSEXESVC.exe.
Registry Key: The EULA acceptance is stored in the registry at HK_USERS\[SID]\Software\Sysinternals\PsExec\EulaAccepted.
Additional reading on PsExec and SMBexec:
Windows Lateral Movement with smb, psexec and alternatives.
https://nv2lt.github.io/windows/smb-psexec-smbexec-winexe-how-to/
Remote Desktop Protocol (RDP)
For RDP-based lateral movement:
Group Membership: Check Event ID 4728 when users are added to the “Remote Desktop Users” group.
Bitmap Cache: RDP client stores bitmaps locally, which can be parsed using tools like RdpCacheStitcher, EnCase, and BMC Tools. These tools can help reconstruct images that were viewed during the session, potentially revealing sensitive information.
Detecting and Hunting Lateral Movement
Detecting PsExec Activity:
Process Creation Events: Event IDs 4688/4689 (or Sysmon Event IDs 1/5).
Service Creation: Event IDs 7045/7036 for PSEXESVC, File creations (Sysmon Event ID 11)
Registry Monitoring: Look for EULA acceptance in the registry.
File Creations: Track the creation of PSEXESVC.exe.
Detecting smbexec Activity:
Lucene-based queries can help identify smbexec usage. For example:
• CommandLine:"powershell.exe -NoP -NoL -sta -NonI -W Hidden -Exec Bypass"
• CommandLine:("\\127.0.0.1\C$\__output" OR "127.0.0.1 AND __output")
• CommandLine:"%COMSPEC% AND /Q AND /c"
• CommandLine:"%COMSPEC%"
• FileName:("execute.bat OR __output")
• EventID:7045 AND ServiceName:"BTOBTO"
To learn more about hunting for Impacket/smbexec, see Riccardo Ancarani’s “Hunting for Impacket” article here:
Ransomware Evolution: Expanding Beyond Windows
Ransomware groups are increasingly targeting non-Windows platforms, including Linux, macOS, and virtualization platforms like VMware's vCenter, vSphere, and ESXi.
Attacks on vSphere Infrastructure:
Tools like SharpSphere allow attackers to gain control over vSphere infrastructure.
Attackers can list VMs, dump memory, or execute code on virtual machines.
Targeting ESXi Servers:
Attackers exploit vulnerabilities in ESXi servers to encrypt multiple VMs simultaneously.
Examples include using custom Python scripts to target ESXi servers.
Ransomware-as-a-Service (RaaS) and ESXi Payloads:
RaaS platforms like LockBit 3.0 and BlackBasta are generating native ESXi ransomware payloads, making it easier for attackers to target virtualized environments.
Incident Response and Forensics on Non-Windows Platforms
Manual Artifact Collection: Before mid-2022, collecting forensic artifacts from ESXi and other Unix-like systems was mostly manual, making it a time-consuming process during incident response.
Unix-like Artifacts Collector (UAC): Developed by Thiago Canozzo Lahr, this tool automates the collection of system artifacts from various Unix-like operating systems, including ESXi, Linux, macOS, and others. This automation improves the speed and efficiency of incident response efforts.
Learning Resources:
Leonard Savina's presentation attaching below
Thiago Canozzo Lahr's presentation attaching below
Conclusion:
By covering all key protocols, tools, detection techniques, and the latest ransomware trends, this blog provides a comprehensive understanding of lateral movement and how to defend against it. Stay vigilant, and make sure to incorporate the detection strategies discussed to protect your network from lateral movement attacks.
Akash Patel
I have created an blog and a pdf file which will help you investigate artifact in source system and destination system. The pdf contain detection or analysis based on Event IDs as well as based on File system artifact link below:


Comments