Lateral Movement Analysis: Using Chainsaw, Hayabusa, and LogParser for Cybersecurity Investigations
- Jan 6
- 9 min read

A few days ago, I received a request through my website from someone working on an incident response case. He mentioned a situation involving 20 endpoints and asked if there was a quicker way to identify lateral movement—specifically, whether users on those endpoints had attempted to log in to other systems and whether those attempts were successful.
He was manually analyzing logs from all 20 endpoints, which was understandably time-consuming and inefficient.
Around the same time, another cybersecurity professional with more t than 20 years of experience reached out, seeking an easy way to identify lateral movement and asking me to teach him how to analyze it.
Frankly, I was surprised. With such extensive experience and a high-level role, I didn’t expect lateral movement analysis to be a pain point for him.
This got me thinking: while most professionals understand what lateral movement is, identifying it during an investigation remains challenging.
Lateral movement analysis requires a deep understanding of logs, artifacts, and various attack vectors, which can seem daunting, even for seasoned Incident Response (IR) and Digital Forensics & Incident Response (DFIR) practitioners.
Inspired by these requests, I decided to simplify things with this article.
Today, I'll discuss three tools that make lateral movement analysis much easier:
Chainsaw
Hayabusa
LogParser
If you're unfamiliar with these tools, I’ve already written detailed guides explaining how they work, which commands to use, and what to expect from them. You can check out the following posts:
However, today we’ll focus solely on using these tools for lateral movement analysis.
-------------------------------------------------------------------------------------------------------------
What Is Lateral Movement?
I won’t delve too much into the basics since most of you already know what lateral movement is. If you don’t, I recommend checking out my articles:
This articles ***covers everything you need to know about manually analyzing lateral movement, using registry , Event IDs, and filesystem****. It’s a great foundation to build your skills before diving into automated tools.



-------------------------------------------------------------------------------------------------------------
Chainsaw: Simplifying Lateral Movement Analysis
Let’s dive into the first tool, Chainsaw, and see how it simplifies log analysis for lateral movement.
I’ll demonstrate how to run a single command in PowerShell and let Chainsaw do the heavy lifting.
Command:
PS E:\Log Analysis Tools\chainsaw_all_platforms+rules+examples\chainsaw> .\chainsaw_x86_64-pc-windows-msvc.exe hunt -r rules\ "E:\Output for testing\logs 123\log123"Chainsaw immediately starts hunting through the logs, isolating critical events that may indicate lateral movement. Below are some screenshots and insights from my analysis.

Screenshot 1: User Remote Access
Chainsaw identified that the user remotely accessed a system (XSPACE2197) using the IP 192.168.30.1.

While this could be legitimate, you’d need to verify it by asking the user or checking the context.
What’s impressive here is how easily Chainsaw pinpoints such activities, saving you time compared to manual log analysis.
Screenshot 2: RDP Logoff Events
Chainsaw highlights RDP logoff events.

Although these don’t directly indicate lateral movement, they’re worth noting when attackers move between systems via RDP and log off after completing their actions.
Screenshot 3: Potential RDP Attack
In this example, Chainsaw identified events showing successful RDP logins, session connections, and disconnections. Here’s what stood out:

The user is Jean-Luc, and the IP 192.168.30.1 suggests activity within a trusted network.
While these behaviors may seem normal, it’s crucial to confirm whether this activity aligns with the user’s routine.
Chainsaw’s ability to filter relevant data means you don’t need to sift through mountains of logs manually. It automates the heavy lifting, allowing you to focus on deeper investigation and validation.
-------------------------------------------------------------------------------------------------------------
A Word of Caution
While tools like Chainsaw automate much of the analysis, ***manual log analysis remains an essential skill for any cybersecurity professional**.
Automated tools like Magnet Axiom and FTK are great, but understanding the underlying artifacts (e.g., $J, $MFT) and
how to analyze them manually is what truly sets you apart as a forensic investigator
-------------------------------------------------------------------------------------------------------------
Hayabusa Tool: Lateral Movement Analysis Made Easy
Hayabusa has quickly become one of the most reliable tools in my log analysis arsenal. It’s versatile, efficient, and saves an incredible amount of time—especially when detecting lateral movement. Let’s dive into how you can leverage Hayabusa specifically for lateral movement detection.
Highlights of Hayabusa in Action
1. When you feed your logs to Hayabusa, it doesn’t just dump all events on you. Instead, it filters and categorizes them into a manageable set of results. For instance:
Input Logs: 12,776 events.
Filtered Suspicious Events: 1,338 events.
2. Hayabusa categorizes the events by their severity:
Critical
High
Medium
Low
Each category is color-coded, making it visually intuitive to spot critical issues at a glance.
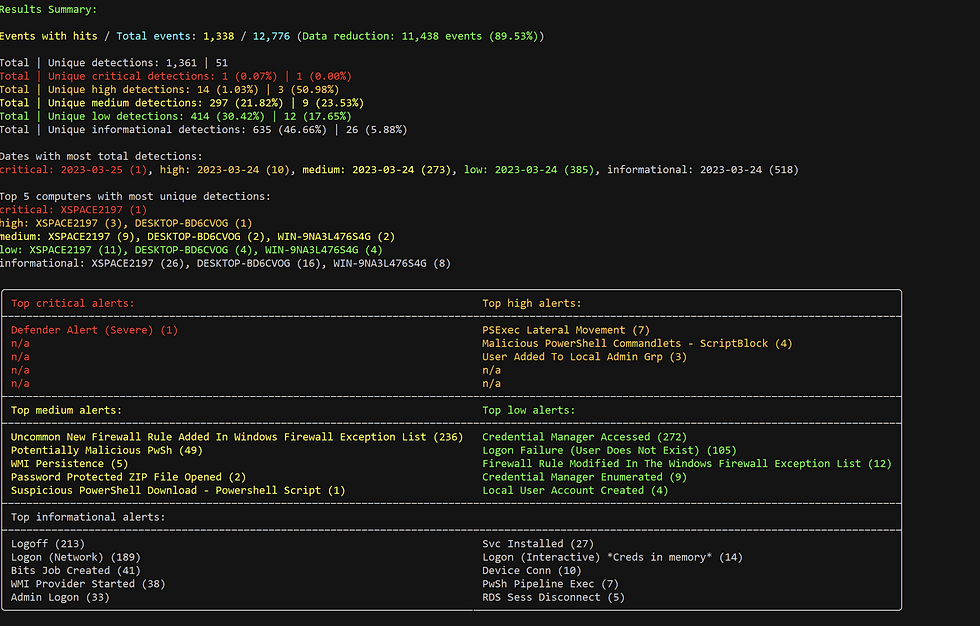
Detecting Lateral Movement
Hayabusa flagged potential lateral movement activities. Here’s how it looked:

In the screenshots below, I’ve highlighted key areas you should focus on when looking for lateral movement indicators. While there are other important artifacts, such as service installations, I’m providing a basic overview of what to watch for when analyzing logs for lateral movement.

At start we had 12,776 events after running hayabusa we only have hits—1339.

If you take a look at the output in the command prompt, you might think, "This analysis isn't for me. How can I make this more manageable and effective?" Don’t worry—I’ve got you covered!.
There’s a streamlined way to analyze this data, and I’ll show you exactly how to make sense of it more efficiently.
Simplifying the Analysis Process
Analyzing these hits manually through the command prompt can quickly become cumbersome. So, let me share a personal method I use to simplify the process:
First, I extract all the data from Hayabusa into a CSV file, using the following command:
PS E:\Log Analysis Tools\hayabusa-2.17.0-win-x64> .\hayabusa-2.17.0-win-x64.exe csv-timeline -d "E:\Output for testing\logs 123\log123" -o output.csv

Next, I use Timeline Explorer to open the CSV file. It’s a fantastic tool for navigating through the extracted timeline data and helps you easily pinpoint areas of interest.

Let’s say I want to focus on a specific lateral movement indicator, like "PSExec Lateral Movement."

Simply search for it in the Excel file, and you’ll get the results—just like the screenshot below.

Suppose I want to investigate "Logon (Network)" events. I can search for that in the CSV and quickly get all the details I need, including the type of logon, user, source computer, and source IP. The ease of this process cannot be overstated.


Why Hayabusa Is My Tool of Choice
If I had to choose one tool for Log Analysis, it would always be Hayabusa. Its seamless integration with timeline data and ability to quickly filter through vast amounts of log data makes it the best choice for me.
Much like KAPE, Hayabusa has become an indispensable part of my inventory.
I’ve been using it for the past three years, and it has come a long way, becoming more efficient and accurate with each iteration.
A big thank you to Yamato Security Group in Japan for creating a tool that truly makes the work of forensic and IR professionals much easier.

-------------------------------------------------------------------------------------------------------------
Log Parser: Building Precise Detection Queries
Recently, I was reflecting on tools like Hayabusa and Chainsaw and wondered:
"Is it possible to build custom queries with exceptions to make detections more precise?"
While these tools are fantastic, they don’t offer much flexibility for creating or applying exceptions directly.
That sparked a thought: why not explore Log Parser for this purpose?
Log Parser uses SQL-like language, which makes it different from other tools. It provides the flexibility to build highly tailored queries, including exceptions, which can significantly enhance detection precision.
A Quick Note on Log Parser
If you're unfamiliar with Log Parser, I’ve written a complete article detailing its features, commands, and use cases. The link is available at the top of this post—feel free to check it out!
Objective: Detecting Lateral Movement
For this experiment, I’ll focus on detecting lateral movement using logs. The primary log source will be security.evtx. There are already commands created to run with logparser and these commands are attached in my article itself.
I felt the need to create new, customized ones. Let’s get started!

Setup and Approach
I’ve collected the logs from one endpoint into a single directory. We’ll primarily work with SQL queries to parse and analyze the data.
Below is the commands I crafted as a starting point:(Worry not at end I will attach text file containing all the query so u can modify as per your need )
1. Query to Detect RDP Logins (Event ID 4624)
Purpose:
RDP is frequently used for lateral movement by attackers to access remote systems. You can use Event ID 4624 (successful logon) to track RDP logins

Usage:
This query will show when a user logs in via Remote Desktop, which can be indicative of lateral movement across machines.
2. Query to Detect Lateral Movement via SMB (Event ID 5140)
Purpose:
Lateral movement often involves SMB (Server Message Block) to access shared resources across systems. Event ID 5140 indicates that a network share was accessed. Monitoring this can help detect unauthorized lateral movement attempts.

Expected Output:
The query will show network share access by users, which could be an indicator of lateral movement.
3. Query to Detect Credential Dumping Tools (Event ID 4688)
Purpose:
Malicious actors often use tools such as Mimikatz or LaZagne to dump credentials during lateral movement. Monitoring process creation events (Event ID 4688) for signs of such tools is important.

Expected Output:
This query will help detect the execution of credential dumping tools used for lateral movement.
4. Query to Detect Abnormal WMI Activity (Event ID 5858)
Purpose:
WMI (Windows Management Instrumentation) is commonly used by attackers for lateral movement. Event ID 5858 represents successful WMI operations. Monitoring this can help detect malicious use of WMI for lateral movement.

Expected Output:
This query will show WMI operations initiated by users, which could indicate lateral movement across systems.
5. Query to Detect Multiple Failed Logins (Event ID 4625)
Purpose:
When attackers attempt to move laterally, they often try brute-forcing credentials. Monitoring for multiple failed logon attempts can help detect these attempts.

Expected Output:
This query will show multiple failed logon attempts, which may indicate brute-force or credential stuffing attacks.
6. Logon and Logoff Activity (Event IDs 4624 and 4634)
Purpose:
These queries track user logons and logoffs, filtering by remote logon types like RDP (Logon Type 10), network logons (Logon Type 3), and other types like unlocking workstations or batch jobs. The goal is to detect unauthorized access or lateral movement, including identifying unusual source IPs and workstations.

7. Process Creation (Event ID 4688):
Purpose:
This query identifies the creation of processes that may be indicative of malicious activity, such as cmd.exe, powershell.exe, wmic.exe, and net.exe. These processes are frequently used for lateral movement, privilege escalation, and other post-exploitation activities. Analyzing the associated command lines and parent processes can reveal suspicious actions.

8. Remote and Network Logons:
Purpose:
Remote and Network Logons: This query monitors network logons (such as those using SMB) and RDP logons (Logon Type 10). It helps track remote access, particularly focusing on user-driven activities and excluding system accounts. This is particularly useful for detecting lateral movement and unauthorized logins from unexpected locations.

9. Service Creation:
Purpose:
This query tracks suspicious service installations that could indicate malicious activity. For example, the creation of services associated with tools like PsExec, powershell.exe, and cmd.exe may point to attackers maintaining persistence or executing lateral movement within a network.

While the rules mentioned earlier offer a great starting point for detecting suspicious behavior using LogParser, you can further fine-tune these queries to create more customized detections.
As you can see, it’s quite simple to adapt and refine these rules to better fit your needs.
With the combination of LogParser, process creation analysis, and remote logon detection, you have a powerful toolset to detect lateral movement in your environment.
I've added the rules in a text file and attached it for you. You may notice that some rules appear to be duplicates. If these aren’t relevant to your needs, feel free to leave them out or modify them to suit other detections. I’ve provided them just for your reference—please don’t get upset with me!LOL
Also, keep in mind that due to Windows updates, some rules might stop working after a few months. Make sure to double-check andtest the rules before running them against your logs.
-------------------------------------------------------------------------------------------------------------
Managing Logs from Multiple Workstations
Now, let’s take this to the next level. Imagine you have 10 workstations, each generating their own security logs, and you collect these logs into separate folders.
Instead of manually running the same command for each folder, which can be time-consuming and inefficient, I’ve got a solution that will make your life easier.

Here’s how it works:
The script I’ve developed will automatically scan multiple folders or subdirectories in a specified root path.

It will identify the Security.evtx logs within each folder, apply your customized detection rules, and generate the output, all with minimal effort on your part. This method streamlines the process and significantly reduces the complexity of manually executing commands for each log file.
A Simple, Effective Approach
This approach ensures that you can scale your detection efforts across many workstations without being bogged down by repetitive tasks. It’s quick, efficient, and easy to implement—exactly what you need when working with large datasets or multiple machines.
-------------------------------------------------------------------------------------------------------------
Get Involved!
If you have any queries, suggestions, or additional detection methods you'd like to share, feel free to reach out! I’m always looking for ways to improve and collaborate. Your ideas could be featured in a future post, and you’ll be credited as the creator!
See you in the next one, where we’ll dive deeper into more exciting techniques and tools. Stay tuned!
-------------------------------------------Dean-----------------------------------------------------

Kommentare