Cloud Incident Response: How to Acquire and Analyze a VM Disk Image in Azure
- Nov 10, 2024
- 4 min read
Updated: Dec 3, 2024

When conducting incident response in the cloud, there often comes a point when logs alone aren’t enough, and we need direct access to data from the affected machine. Acquiring an image of a virtual machine (VM) in Azure and analyzing it in the cloud can save both time and egress costs compared to downloading it. This guide will walk you through each step in setting up and performing forensic analysis in the cloud, using a dedicated “Forensic VM” to examine a disk image created from a “Victim VM.”
Steps to Perform In-Cloud Forensic Analysis:
Step 1: Snapshot the OS Disk from the Victim VM
To start, take a snapshot of the VM’s disk. A snapshot is a full, read-only copy of the disk at a specific point in time.
Locate the Victim VM in the Azure portal and navigate to its disk.
Create a Snapshot: Select the “Snapshot” option for the disk. Make sure the VM is running, as snapshots can be created on active VMs.
Choose Snapshot Type: Select “Full” for a complete copy of the disk. Use “Incremental” if you’re doing routine backups.
Name the Snapshot: Assign a descriptive name (e.g., victim) to avoid confusion in later steps.
Azure storage costs apply to snapshots ($0.05/GB/month for standard and $0.132/GB/month for premium). For most investigations, snapshotting only the OS disk is sufficient. However, if the VM has data disks, you may need snapshots of these too.


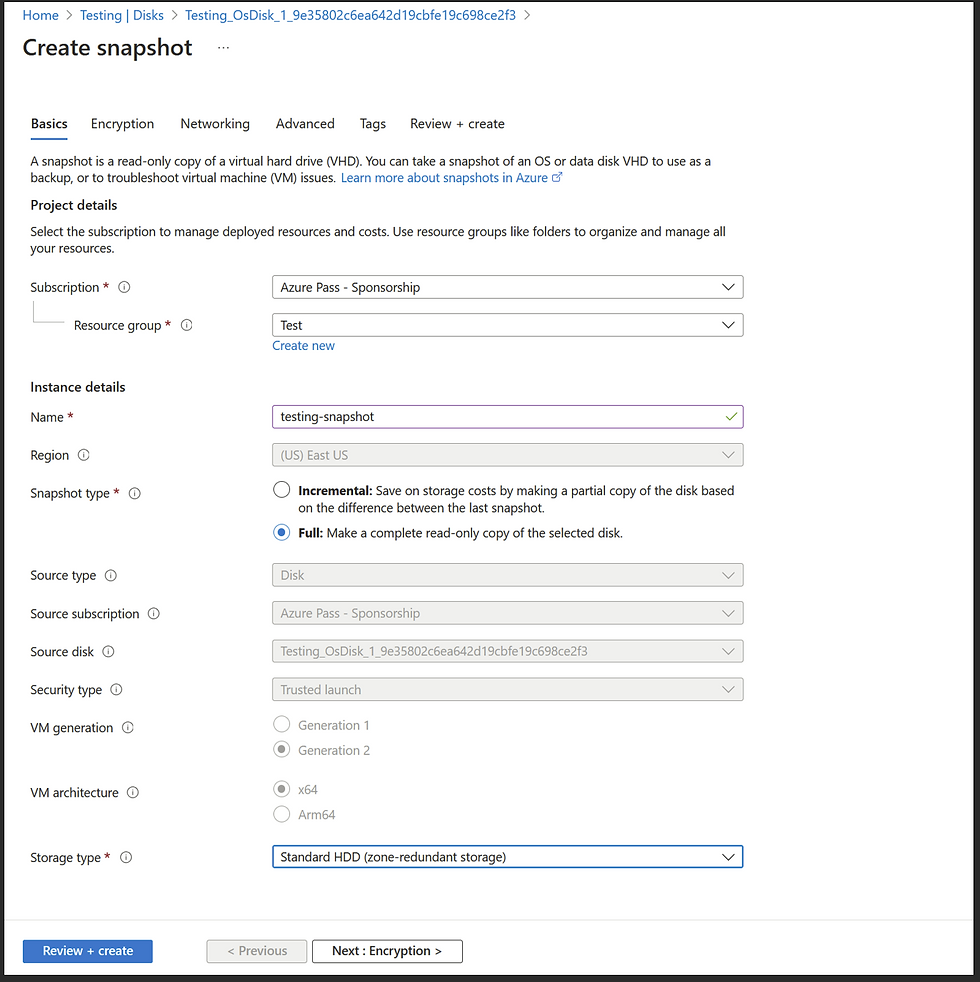
Step 2: Create a New Disk from the Snapshot
The snapshot data now needs to be applied to a new disk, making it accessible for analysis.
Create a Disk from the Snapshot: In the Azure portal, go to “Create Disk” and select “Snapshot” as the source type.
Name the Disk: Name it similarly to the snapshot, adding -disk at the end (e.g., victim-vm-os-disk) for easy identification.
Select Disk Type: Choose Premium SSD for faster data processing speeds during forensic analysis. If cost is a concern, you can delete the snapshot after this step, but keeping it is advisable as a backup.
Create Disk: Confirm and create the disk.
This disk now holds all data from the snapshot and is ready to be attached to a VM for analysis.


Once created search for disks (You will find created disk there)

Step 3: Create the Forensic VM
To analyze the imaged disk, create a separate VM called the “Forensic VM” with adequate resources for your forensic tools.
Select VM Specifications: Choose a VM size with a robust CPU (4 vCPUs) and memory (16GB) to handle the processing demands of forensic tools.
Create OS Disk: During setup, the Forensic VM will have its own OS disk where you can install forensic software and store results.
Data Disk Selection: Under “Data Disks,” select “Attach an Existing Disk” and attach the disk you created in Step 2. If you forget this step, shut down the VM before attaching the disk to prevent corruption.
Location and Region: Make sure the Forensic VM is created in the same region as the victim VM disk for performance optimization.
This VM will host your forensic tools, such as KAPE, and provide an isolated environment for analysis.



Step 4: Mount the Disk in the Forensic VM
Once the Forensic VM is running, access the imaged disk by mounting it.
Access Disk Management: In the VM’s Disk Management window, you will see:
Disk 0: The Forensic VM’s OS disk (typically C:).
Disk 1: Temporary storage (typically D:), which is not persistent.
Disk 2: The attached disk from the victim VM.
Bring Disk 2 Online: Right-click on Disk 2 and select “Online.” Windows will assign a letter to each partition.
Access the OS Partition: The OS partition will appear as another drive (e.g., G:), which you can now investigate.
Ensure you avoid writing to this disk during analysis to maintain the integrity of the data. If any corruption occurs, simply repeat from Step 2 using the original snapshot.
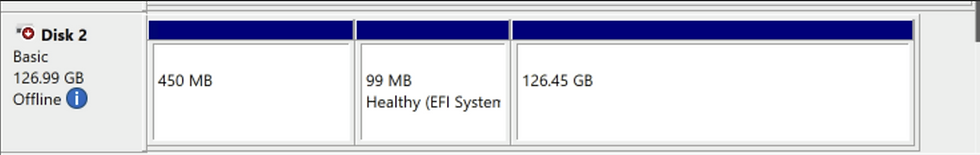

Step 5: Run Forensic Tools on the Forensic VM
With the disk mounted, you can now use forensic tools to analyze the image.
Install Forensic Tools: Tools like KAPE, FTK Imager, or any preferred forensic software can be installed on the Forensic VM’s OS disk.
Perform Analysis: Analyze the OS partition to retrieve relevant evidence. Remember that this disk is writable, so take care not to alter the contents unintentionally.
If you need a point-in-time copy for future analysis, consider using the snapshot or taking another snapshot of the newly created disk.

-------------------------------------------------------------------------------------------------------------
Optional: Alternative Snapshot Access Methods
For scenarios that require additional tools, downloading the snapshot as a virtual hard disk (VHD) can be useful.
Export the Snapshot: Select the snapshot in the Azure portal, navigate to “Snapshot Export,” and generate a one-time URL for downloading.
Use AzCopy for Speed: To accelerate the download, use the AzCopy tool with the command:
azcopy cp "--snapshot URL--" "c:\programfiles\snapshot.vhdx" --check-md5 nocheckVHD Advantages: Direct VHD access enables automation and integration with tools that may require offline data access. However, be mindful of the potential data egress costs and long download times.
Forensic VM Image Creation for Future Use
To streamline future investigations, Azure offers ways to create and share VM images.
Create an Image: Create a VM with all your forensic tools installed, then save it as an image in the Azure Compute Gallery. This enables quick setup of similar VMs for future investigations.
Use Azure Image Builder (Advanced): If you prefer customization, use Azure Image Builder to craft an image from scratch.
This setup is ideal if you need to transfer or reuse the Forensic VM across different regions, subscriptions, or resource groups.
-------------------------------------------------------------------------------------------------------------
Summary
Using Azure’s in-cloud investigation capabilities, you can create snapshots, build forensic VMs, and attach imaged disks to streamline your incident response process. By performing forensic analysis in the cloud, you can bypass data egress costs, reduce transfer times, and work efficiently on even large data sets. With this guide, you have a complete roadmap for setting up in-cloud forensic analysis and enhancing your response capabilities in Azure.
Akash Patel
----------------------------------------------------------------------------------------------------------Special Thanks (Iqra)
I would like to extend my heartfelt gratitude to one of my dearest colleagues, a Microsoft Certified Trainer, for her invaluable assistance in creating these articles. Without her support, this would not have been possible. Thank you so much for your time, expertise, and dedication!
-------------------------------------------------------------------------------------------------------------




Comments