Firefox Browser History for Forensic Investigations
- Mar 8
- 2 min read

When investigating digital evidence, a browser’s history can be a goldmine of information. Firefox, like other modern browsers, maintains extensive records of user activity, storing this data in the places.sqlite database. This database can provide critical insights into a user’s online behavior, revealing visited websites, timestamps, and other relevant metadata.
-----------------------------------------------------------------------------------------------------------
Understanding Firefox History Storage
Firefox originally stored browsing history for a fixed 90-day period, but since version 4, the duration is dynamically determined based on system resources. This means history data can span months or even years, sometimes reaching hundreds of thousands of entries.
Key Tables in places.sqlite
To extract meaningful information, investigators must focus on two primary tables:
moz_places: Contains URLs, visit counts, titles, and metadata related to web visits.
moz_historyvisits: Stores detailed records of each visit, including timestamps, referrers, and visit types.

-----------------------------------------------------------------------------------------------------------
Extracting Useful Information
Identifying Frequently Visited Sites
The visit_count column in moz_places helps determine which sites a user visited most frequently.

Pages with a visit count greater than one suggest intentional and repeated access.
Creating a Timeline of Activity
Each visit to a webpage is recorded in moz_historyvisits, and the visit_date field provides timestamps.

By sorting entries by date, analysts can track user activity over specific time frames.
Determining User Intent
The typed field in moz_places indicates if the URL was manually entered.
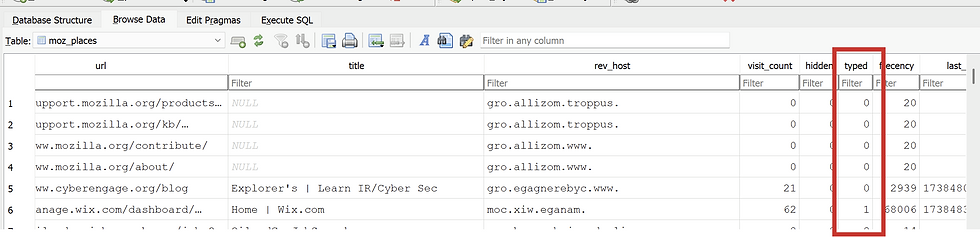
The from_visit attribute reveals the previous page that led to the current visit.

The visit_type field categorizes how a page was accessed.

-------------------------------------------------------------------------------------------------------------
Co-relating data from moz-place to moz_history visit to get an timestamp

------------------------------------------------------------------------------------------------------------
Decoding the visit_type Field
The visit_type field in moz_historyvisits provides insight into why a URL was recorded:

Type | Description |
1 | User followed a link, and the page was loaded |
2 | User typed the URL to get to the page (with or without auto-complete) |
3 | User followed a bookmark to get to the page |
4 | Indicates some inner content was loaded, such as images and iframes |
5 | Page accessed due to a permanent redirect (HTTP 301 status code) |
6 | Page accessed due to a temporary redirect (HTTP 302 status code) |
7 | File indicated by history was downloaded (non-HTML content) |
8 | User followed a link that loaded a page in a frame |
9 | Page was refreshed/reloaded |
------------------------------------------------------------------------------------------------------------
Handling PRTime Timestamps
Firefox stores timestamps in PRTime format (microseconds since January 1, 1970). To convert a value like 1736802810848000 to a readable format, analysts can use tools like SQLite queries, Python scripts, or online converters.

or
Using NirSoft BrowsingHistoryView for Analysis
While manually parsing the places.sqlite database provides deep insights, tools like NirSoft’s BrowsingHistoryView streamline the process:
Mount Evidence: Point the tool to the browser profile stored in forensic images or live systems.
Review Data: Filter and analyze history entries from multiple browsers in one interface.
Export Findings: Save reports in text or HTML formats for documentation.

------------------------------------------------------------------------------------------------------------
Final Thoughts
Firefox’s history database is an invaluable asset for digital investigations. By leveraging both manual database queries and forensic tools, analysts can reconstruct online activity with precision. Understanding how this data is structured and retrieved allows for effective forensic analysis, ultimately helping to establish patterns, verify timelines, and uncover digital evidence.
--------------------------------------------Dean-----------------------------------------------

Comments