Cloud Services: Understanding Data Exfiltration and Investigation Techniques
- Oct 21, 2024
- 5 min read

In today’s cybercrime landscape, attackers are increasingly turning to cloud services for data exfiltration. While this presents additional challenges for defenders, it also offers opportunities to track and mitigate the damage.
The Shift to Cloud-Based Exfiltration
Cloud storage providers have become popular among attackers because they meet key requirements:
Speed and availability: Attackers need fast, scalable infrastructure to quickly move large amounts of stolen data.
Cost-efficiency: Many cloud services offer significant storage at minimal or no cost.
Less visibility: Cloud platforms are generally not on security blacklists, making it harder for traditional defenses to detect the exfiltration.
Attackers streamline their operations by using cloud platforms to exfiltrate data. In some cases, the copy stored in the cloud is the only copy the attackers have, which they later use to demand ransom or release the data publicly. The efficiency of using a single storage location means attackers can avoid time-consuming data copying, making their extortion schemes quicker and harder to track.
Fast Response from Cloud Providers
While attackers use cloud platforms, the providers have become more cooperative in helping victims. Many cloud providers act quickly on takedown requests, often removing malicious data within hours or minutes. This means that although cloud services are used for exfiltration, they are rarely used for data distribution because of the prompt responses from the providers.
However, gaining access to the cloud shares used for exfiltration can provide valuable insights for the victim. Accessing the attacker’s cloud storage allows investigators to:
Assess the extent of the data stolen.
Make the data unusable by inserting traps like canary tokens or zip bombs.
Gather information on other potential victims, especially when attackers reuse cloud accounts across multiple breaches.
In some instances, investigators have been able to notify other breached organizations before the attackers could fully execute their plans, offering a rare preemptive defense against encryption or further exfiltration.
----------------------------------------------------------------------------------------------------------
Investigating the Exfiltration Process
During investigations, we often find that attackers have used common tools and techniques to identify and exfiltrate sensitive data from an organization’s network. Ransomware cases frequently reveal how attackers plan their operations, from identifying sensitive file shares to the exfiltration itself. The following steps provide an outline of the typical exfiltration process:
1. Scanning for Sensitive Shares
Attackers often start by scanning the network for shared folders that might contain sensitive data. Tools like SoftPerfect Network Scanner are frequently used for this task. These tools display available share names and show which users are logged in to the machines, helping attackers prioritize targets.
From an investigative standpoint, defenders can sometimes recover partial screenshots or cache files of the attacker’s scanning activity. For example, attackers may be particularly interested in machines where admin users are logged in or shares named after departments like “HR,” “Finance,” or “Confidential.” Fortunately, these shares may not always contain the most critical data, but they still serve as key entry points for attackers.
2. Tracking the Attackers’ Actions
Understanding what the attackers were looking for and where they browsed can be crucial for assessing the damage. To do this, defenders can rely on artifacts like MountPoints and Shellbags, both of which provide forensic insights into the attackers’ activities.
MountPoints: These are stored in registry keys and show what external storage devices (like USB drives) or network shares were mounted. By examining the registry, investigators can track what shares attackers connected to using the “net use” command. Tools like Registry Explorer by Eric Zimmerman are particularly useful for browsing these entries.
Shellbags: These artifacts store user preferences for Windows Explorer windows, including the location and size of the windows. They also store the directory paths the user browsed. Since Shellbags are stored per user, investigators can pinpoint specific actions by the attacker, even tracking when and where they navigated. Shellbag Explorer is another tool by Zimmerman that helps present this data in a clear, tree-like structure.
When attackers use an account that should never have interactive sessions (such as a service account), Shellbags allow investigators to reconstruct where they navigated using Windows Explorer, complete with timestamps.
----------------------------------------------------------------------------------------------------------
Tools Used by Attackers for Exfiltration
In our investigations, we frequently encounter two tools for data exfiltration: rclone and MegaSync. Both tools allow for efficient, encrypted data transfer, making them ideal for attackers.
1. MegaSync
MegaSync is the official desktop app for syncing with Mega.io, a cloud storage platform popular with attackers due to its encryption and large storage capacity. While the traffic and credentials for MegaSync are heavily encrypted, the application generates a logfile in binary format.
Tools like Velociraptor can parse these log files to extract the names of uploaded files, giving investigators a clearer idea of what was exfiltrated.2. Rclone
Rclone is a command-line tool for managing files across more than 40 cloud storage platforms, including Mega.io. Its appeal lies in its support for HTTPS uploads, which bypass many traditional security filters like FTP.
Attackers often create a configuration file (rclone.conf) to store credentials and other transfer settings, speeding up the exfiltration process by minimizing the number of commands they need to enter. Investigators can target these configuration files, which hold valuable information such as the cloud service being used, stored credentials, and more. In many cases, the configuration file may be encrypted, but attackers occasionally decrypt certain files to prove they have the keys. Investigators can sometimes trick the attackers into decrypting the rclone.conf file, allowing them to gain access to the exfiltration details.
Alternative Techniques for Recovering Exfiltration Data
Even if direct access to the rclone configuration is not possible, defenders can use more advanced methods like volume snapshots and string searches to recover artifacts related to the exfiltration.
Volume snapshots: These provide older versions of a hard drive, akin to Apple’s Time Machine. Although attackers often try to delete these snapshots, tools like vss_carver can help recover them, providing valuable forensic data.
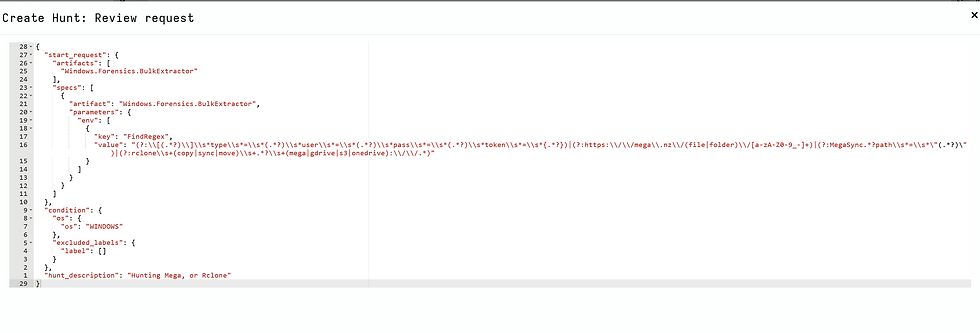
String searches: Tools like bulkextractor and YARA can search hard drives and memory for residual traces of configuration files or rclone-related artifacts, helping to uncover more about the attackers’ activities.
Regex combined for searching Mega and rcloneIn some cases, investigators can even use these methods to track down the attackers’ infrastructure and work with law enforcement to take further action. Cloud providers often have detailed logs showing when the data was uploaded, whether it was downloaded again, and from where
----------------------------------------------------------------------------------------------------------
Conclusion
As attackers increasingly leverage cloud services to exfiltrate stolen data, organizations need to adapt their incident response strategies accordingly. Understanding how attackers use tools like rclone and MegaSync can help defenders detect exfiltration attempts faster and take steps to mitigate the damage. By carefully analyzing forensic artifacts like MountPoints, Shellbags, and volume snapshots, investigators can reconstruct attacker activities and gain insight into the extent of the breach.
Akash .Patel


Comments