The Truth About Changing File Timestamps: Legitimate Uses and Anti-Forensics: Timestomping
- Mar 14, 2024
- 4 min read
Updated: Feb 17
Changing a file’s timestamp might sound shady, but there are actually some valid reasons to do it. At the same time, cybercriminals have found ways to manipulate timestamps to cover their tracks.
Let’s break it down in a way that makes sense.
When Changing Timestamps is Legitimate
Think about cloud storage services like Dropbox. When you sync your files across multiple devices, you’d want the timestamps to reflect when the file was last modified, not when it was downloaded to a new device.
But here’s the problem: when you install Dropbox on a new computer and sync your files, your operating system sees them as “new” files and assigns fresh timestamps.
To fix this, cloud storage apps like Dropbox adjust the timestamps to match the original modification date. This ensures your files appear the same across all devices. It’s a perfectly legitimate reason for altering timestamps and helps keep things organized.
---------------------------------------------------------------------------------------------------------
If you waana learn about cloud storage forensic including dropbox, box, onedrive, Box do check out articles written by me link below happy learning
--------------------------------------------------------------------------------------------------------
So where were we! Yeah, lets continue
When Changing Timestamps is Suspicious
Hackers and cybercriminals love to manipulate timestamps too, but for completely different reasons. A common trick is to disguise malicious files by changing their timestamps to blend in with legitimate system files.
For example
if a hacker sneaks malware into the C:\Windows\System32 folder, they can rename it to look like a normal Windows process. But to make it even less suspicious, they’ll modify the timestamps to match those of other system files.
This sneaky technique is called timestomping.
How Analysts Detect Fake Timestamps
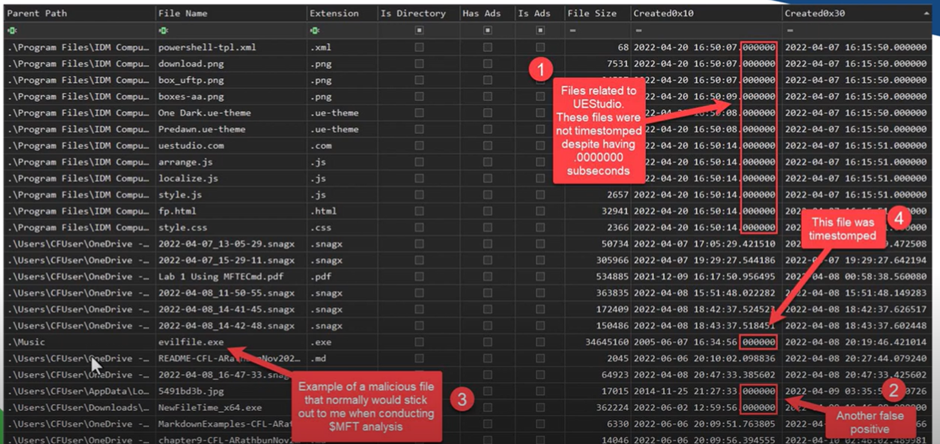
Security analysts have developed several methods to spot timestomping. In the past, it was easier to detect because many tools didn’t set timestamps with fractional-second accuracy. If a timestamp had all zeros in its decimal places, that was a red flag.
Example:
Timestamps
Time stomping in $J
2. Time Stomping in $MFT**(Very Important)
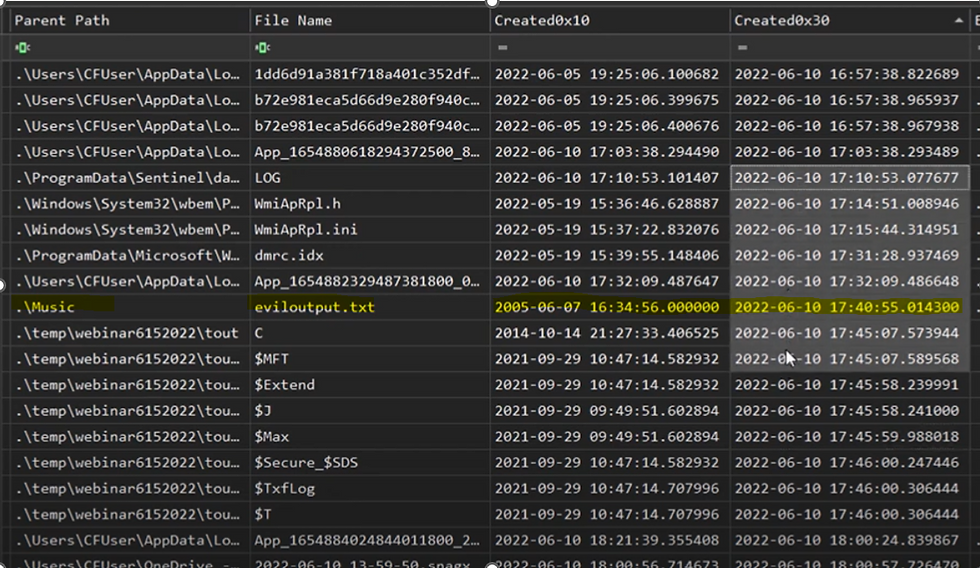
If you see screenshot attacker time stomped the eviloutput.txt they changed timestamp(0x10) to 2005 using anti forensic tool but as anti forensic tool do not modify (0x30) which is showing they original timestamp when file is created
3. Another example
But today, newer tools allow hackers to copy timestamps from legitimate files, making detection trickier.
Here’s how experts uncover timestamp manipulation:
Compare Different Timestamp Records
In Windows, files have timestamps stored in multiple places, such as $STANDARD_INFORMATION and $FILE_NAME metadata. If these don’t match up, something suspicious might be going on.
Tools like mftecmd, fls, istat, and FTK Imager help with these checks.
Look for Zeroed Fractional Seconds
Many timestomping tools don’t bother with precise sub-second timestamps. If the decimal places in a timestamp are all zeros, it could indicate foul play.
Tools: mftecmd, istat.
Compare ShimCache Timestamps
Windows tracks when executables were first run using a system feature called ShimCache (AppCompatCache). If a file’s recorded modification time is earlier than when it was first seen by Windows, that’s a big red flag.
Tools: AppCompatCacheParser.exe, ShimCacheParser.py.
Check Embedded Compile Times for Executables
Every executable file has a compile time embedded in its metadata. If a file’s timestamp shows it was modified before it was even compiled, something’s off.
Tools: Sysinternals’ sigcheck, ExifTool.
Analyze Directory Indexes ($I30 Data)
Sometimes, old timestamps are still stored in the parent directory’s index. If a previous timestamp is more recent than the current one, it’s a clue that someone tampered with it.
Check the USN Journal
Windows keeps a log (USN Journal) of file creation events. If a file’s creation time doesn’t match the time the USN Journal recorded, that’s a clear sign of timestamp backdating.
Compare MFT Record Numbers
Windows writes new files sequentially in the Master File Table (MFT).
If most files in C:\Windows\System32 have close MFT numbers but a backdated file has a much later number, it stands out as suspicious.
Tools: mftecmd, fls.
Real-World Example
Security analysts at Dean service organization investigated a suspicious file (dean.exe) in
C:\Windows\System32. Even though its timestamps matched legitimate files, further checks revealed:
$STANDARD_INFORMATION creation time was earlier than $FILE_NAME creation time.
The fractional seconds in its timestamp were all zeros.
The executable’s compile time (found via ExifTool) was newer than its modification time.
Windows’ ShimCache recorded a modification time that was later than the file system timestamp.
These findings confirmed the file had been timestomped, helping the team uncover a hidden malware attack.
-------------------------------------------------------------------------------------------------------------
All anti forensic tool have one thing in common they mostly modify $SI Timestamp. They do not modify the $FN time stamp. So comparing these two time stamp in timeline explorer can help to identify time stopping.
-------------------------------------------------------------------------------------------------------------
Now keep in mind as normal there might be False positive while analyzing the $MFT for time stomped this thing must be understand by analyst
Screen connect example of timestomp:
The Bottom Line
Timestamp manipulation is a double-edged sword. While cloud storage services use it for legitimate reasons, hackers exploit it to hide malicious files. Security analysts have developed multiple ways to detect timestomping, but modern tools make it harder than ever to spot.
So, the next time you see a file with a suspiciously old timestamp, don’t just take it at face value. There might be more going on under the surface!
----------------------------------------------Dean----------------------------------------------







Comentários