Analyzing and Extracting Bitmap Cache Files from RDP Sessions
- Aug 24, 2024
- 3 min read

When dealing with Remote Desktop Protocol (RDP) sessions on Windows, one of the often overlooked yet valuable artifacts is the RDP bitmap cache. This cache, designed to enhance performance by storing screen sections that don't change often, can be crucial in forensic investigations.
Understanding the Purpose of RDP Bitmap Cache Files
The primary purpose of the RDP bitmap cache is to improve performance by caching screen sections that change infrequently. Instead of redrawing the same portions of the screen multiple times during a session, the cache allows the system to pull the image from local storage. This leads to a smoother and more efficient user experience, especially in sessions where certain parts of the screen remain static.
However, from a forensic perspective, these cached files can be a goldmine of information. By extracting and analyzing the bitmap cache, forensic analysts can potentially uncover information such as file names, icons, and partial screen contents from an RDP session.
Location of Cache Files
The cache files are stored in the user profile directory, and their location varies depending on the version of Windows:
Windows 7 and later: C:\Users\[user]\AppData\Local\Microsoft\Terminal Server Client\Cache\*
Pre-Windows 7: C:\Documents and Settings\[user]\Local Settings\Application Data\Microsoft\Terminal Server Client\Cache\*
Each user profile on a Windows machine will have its own cache files stored in the respective directory. These files contain the cached bitmap data from RDP sessions, making them valuable for forensic analysis.
Extracting and Analyzing Bitmap Cache Files
Several tools are available for extracting and analyzing these bitmap cache files.
BMC Tools
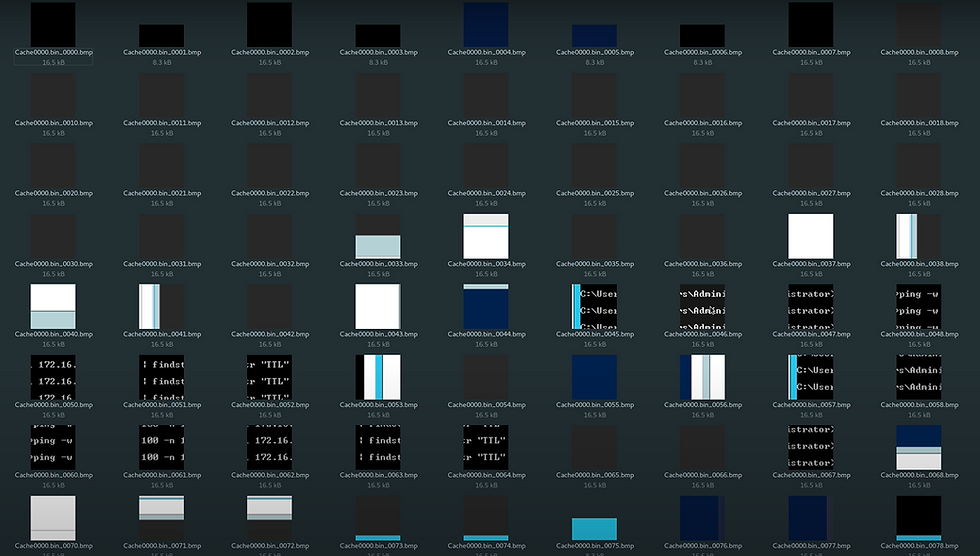
Description: BMC Tools is a free and open-source Python script that extracts and analyzes cached bitmap files. It's a powerful tool for forensic investigations, allowing analysts to reconstruct parts of the screen from an RDP session. However, it's worth noting that BMC Tools doesn't automatically reassemble the complete screen.
Output will look like below after running above tool
Usage: After extracting the cache files using BMC Tools, forensic analysts can manually analyze and piece together the images. The tool's output can help uncover significant details, but it requires careful examination to reconstruct meaningful visuals.
GitHub Repository: https://github.com/ANSSI-FR/bmc-tools
EnCase Script - "RDP Cached Bitmap Extractor"
Description: This script, compatible with the commercial EnCase forensic software, allows for the extraction of cached bitmap images. EnCase is a widely used tool in forensic investigations, and this script integrates seamlessly with its ecosystem.
Usage: Using this script within EnCase, analysts can extract and analyze bitmap cache files. However, it requires a licensed copy of EnCase, which may be a limitation for some forensic teams.
Limitation: EnCase's script also doesn't reassemble the full screen, but it provides a robust framework for extracting and working with cached data.
RdpCacheStitcher
Description: This tool, developed by the Bundesamt für Sicherheit in der Informationstechnik (BSI), provides a user interface for creating collages manually from the output of tools like BMC Tools. It's a useful tool for visualizing and manually piecing together cached bitmap files.
Usage: After extracting images with tools like BMC, RdpCacheStitcher allows analysts to arrange and stitch together these images into a coherent collage. The interface simplifies the manual reconstruction process.
GitHub Repository https://github.com/BSI-Bund/RdpCacheStitcher
BriMor Lab’s “rdpieces”
Description: rdpieces is a Perl script designed to automatically rebuild screenshots from cached bitmap files. It attempts to automate the tedious process of piecing together bitmap fragments, potentially saving time for forensic analysts.
Usage: While not perfect, rdpieces offers a more automated approach to reconstructing screens from cached data. However, the accuracy of the reconstruction may vary depending on the complexity of the cached files.
GitHub Repository: https://github.com/brimorlabs/rdpieces?tab=readme-ov-file
Output:
Challenges in Reassembly
One of the significant challenges in working with RDP bitmap cache files is reassembling the images. The cache files aren't written in a linear or predictable order. Various factors, such as mouse movement or screen changes, can affect the order of cached tiles. As a result, reconstructing a complete image from these cached tiles is often compared to solving a jigsaw puzzle.
While tools like rdpieces attempt to automate this process, the reconstruction isn't always perfect. Forensic analysts must often rely on manual intervention to piece together significant details such as file names, desktop icons, and portions of the screen background.
Conclusion
The extraction and analysis of bitmap cache files from RDP sessions offer a unique avenue for forensic investigation. Tools like BMC Tools, RdpCacheStitcher, and rdpieces provide a range of options for working with these cached images, each with its strengths and limitations. While automated reconstruction is challenging, these tools, combined with manual analysis, can help forensic investigators uncover valuable insights from RDP sessions.
Akash Patel


Comments