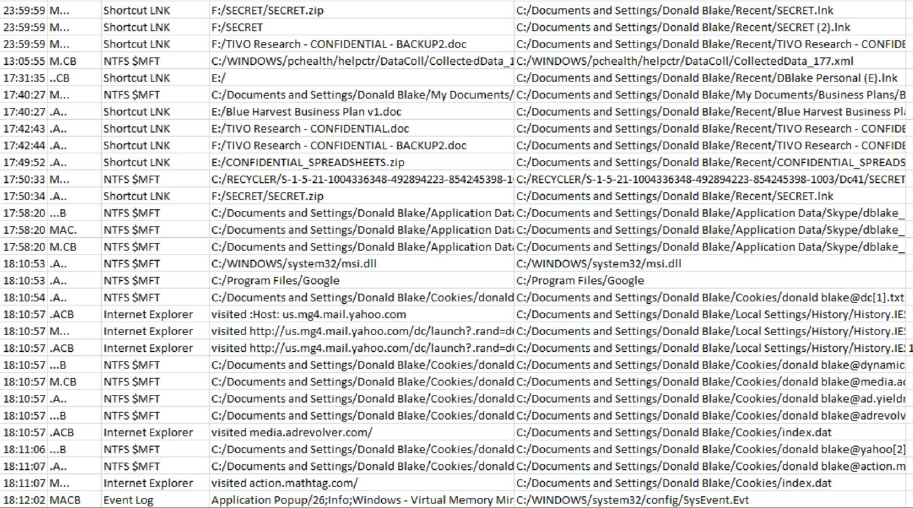
Lets start with an example:
The two drive letters present that could indicate USB/external device activity are "E:" and "F:".
The creation of a LNK file for "E:\V" indicates that a device was inserted, likely an external device such as a USB drive, and opened in something like File Explorer. Several LNK files were created immediately following this event, suggesting that they were opened from the external device.
Internet Explorer was likely used to surf the web when the user accessed their webmail account. This can be inferred from the IE history entries in the timeline, which show activity related to accessing a webmail account.
The event log entry near the bottom of the timeline can provide further information about system activity, such as application launches, system reboots, or user logins.
Live attack example:
Account Logon: The account logs in as a local administrator, indicating privileged access to the system (EIDs 4624/4672/4776) at 22:58:10.
Executable Creation: A new executable, spinlock.exe, is created in the C:\Windows\System32 folder at 22:59:43. This activity raises suspicion as it involves the creation of a potentially malicious file in a critical system directory.
Application Execution: Spinlock.exe and Netstat are executed at -23:09:26 and -23:10:02, respectively, suggesting further system exploration or potential malicious activity.
Directory Creation: The creation of the C:\Windows\System32\dllhost directory at 23:35:07 may indicate attempts to hide or obfuscate malicious files or activities within a system directory.
Registry Modification: Modification of the \services\Netman\domain registry key, which contains an interesting URL, occurs at 23:42:04. This modification could be indicative of attempts to manipulate system configurations or establish persistence.
Suspicious Executables: Svchost.exe and a.exe are executed for the first time, with the latter being highly suspicious.
Star Rule:
Determine Timeline Scope: Analyze key questions and case type to identify the timeframe during which the suspicious activity occurred. This helps narrow down the scope of the timeline analysis and manage data volume.
Narrow Pivot Points: Identify specific time-based or file-based pivot points closest to the suspected incident. This focuses the analysis on relevant data and reduces noise.
Determine the Best Process for Timeline Creation: Decide whether to create a super timeline or a targeted timeline based on required data sources and investigative needs. Super timelines cover a broad range of data sources, while targeted timelines focus on specific sources.
Filter Timeline: Filter timeline data to include only relevant information, de-duplicating and eliminating unnecessary entries. Keywords can help identify and extract relevant pivot points.
Analyze Timeline: Focus on analyzing the context of evidence discovered, examining activities before and after each pivot point to understand user behavior and the sequence of events. Reference tools such as the Windows Forensic Analysis Poster for interpretation.





Comments